With the goal of strengthening Switzerland’s cyber resilience, the Swiss National Cyber Security Centre (NCSC) and the Swiss National Test Institute for Cybersecurity (NTC) have piloted a test for security vulnerabilities of QGIS Server and the QGIS Web Client (QWC2) (besides TYPO3 as another example of an open-source software used by Swiss authorities).
A report of the findings (pdf, in English) is available as well as a press release summarizing the most important findings:
The aim was to technically test two OSS products that are widely used and relevant in public administration, TYPO3 and QGIS, identify vulnerabilities, and work with the developer community to fix them. (…)
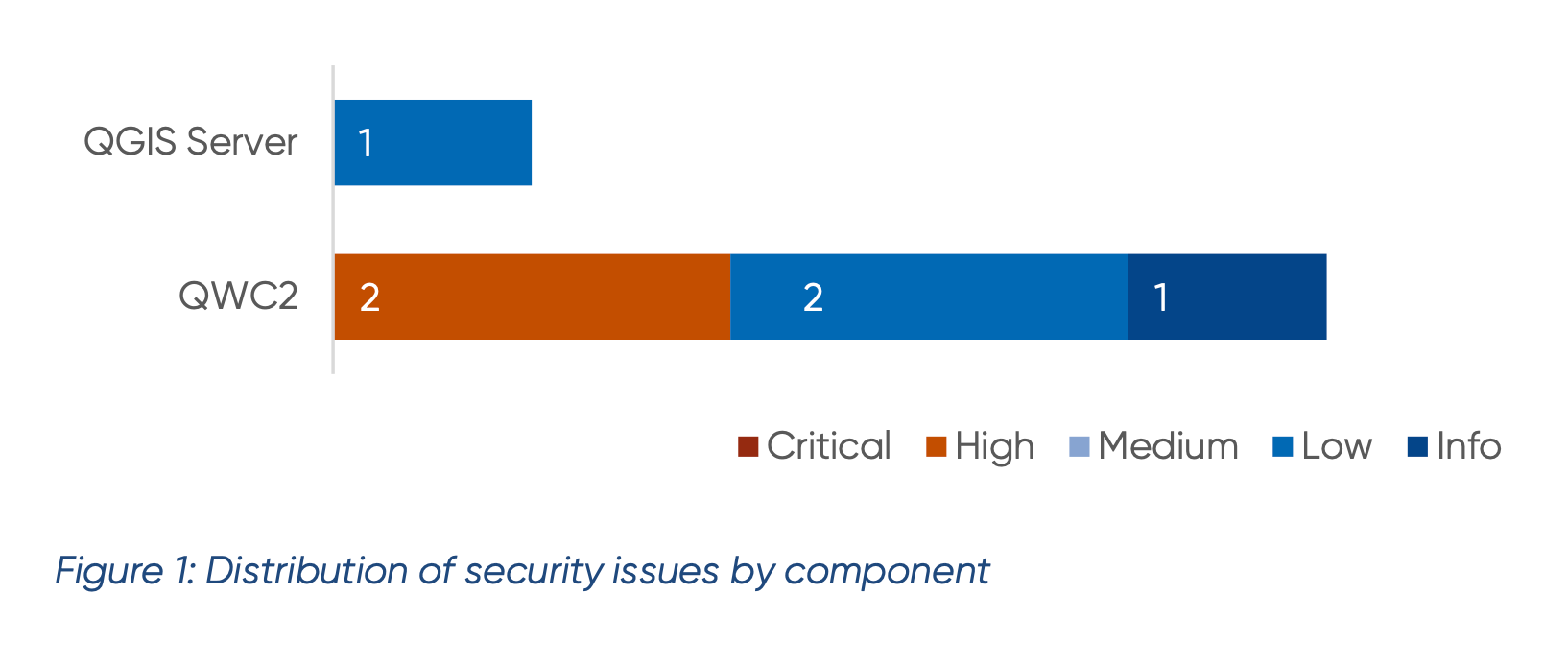
A total of six vulnerabilities were identified: One vulnerability classified as low severity on the QGIS server and five vulnerabilities on the QGIS web client, two of which were rated as ‘high’. All relevant security vulnerabilities were fixed by the responsible open source development teams within the 90-day deadline. The updated software versions are available for download and the technical details are documented in the test reports and the NTC’s Vulnerability Hub.
Great to see that the Swiss government funded the testing. And of course also that no critical issue was identified and that all findings were quickly resolved by the development teams.